Nist Software Security Standards And Guidelines

Covered information disseminated by nist will comply with all applicable omb guidelines doc guidelines and nist guidelines.
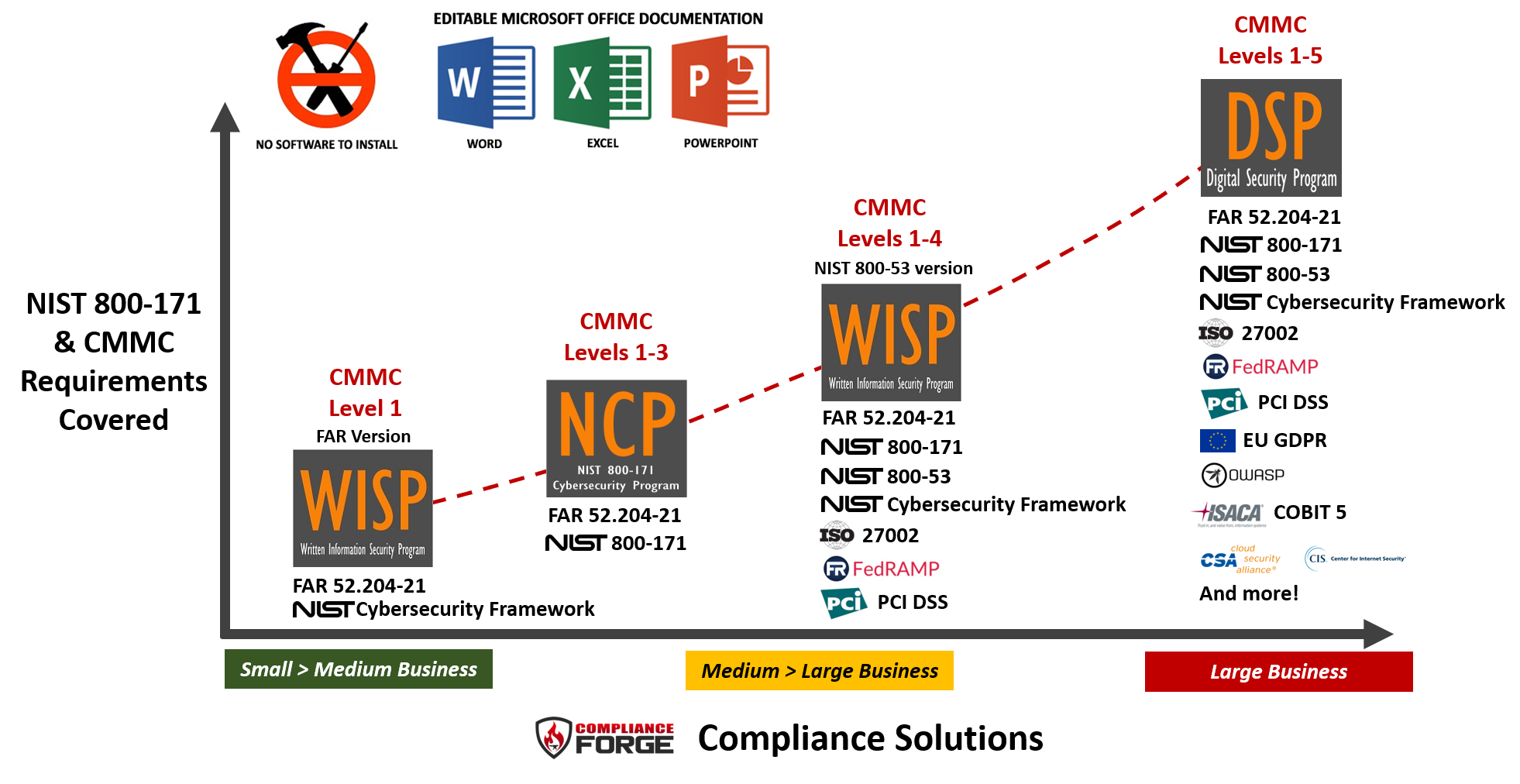
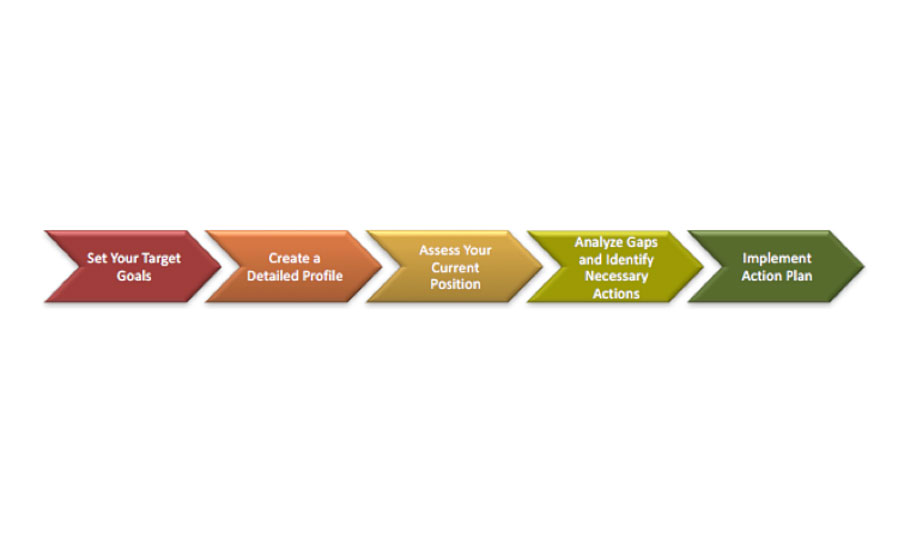
Nist software security standards and guidelines. Nist also assists those agencies in protecting their information and information systems through cost effective programs. This article describes software standards and their characteristics. Development considerations for programmers using standards are explained as well. Nist verifies cryptographic modules based on cryptographic standards through the cryptographic module validation program.
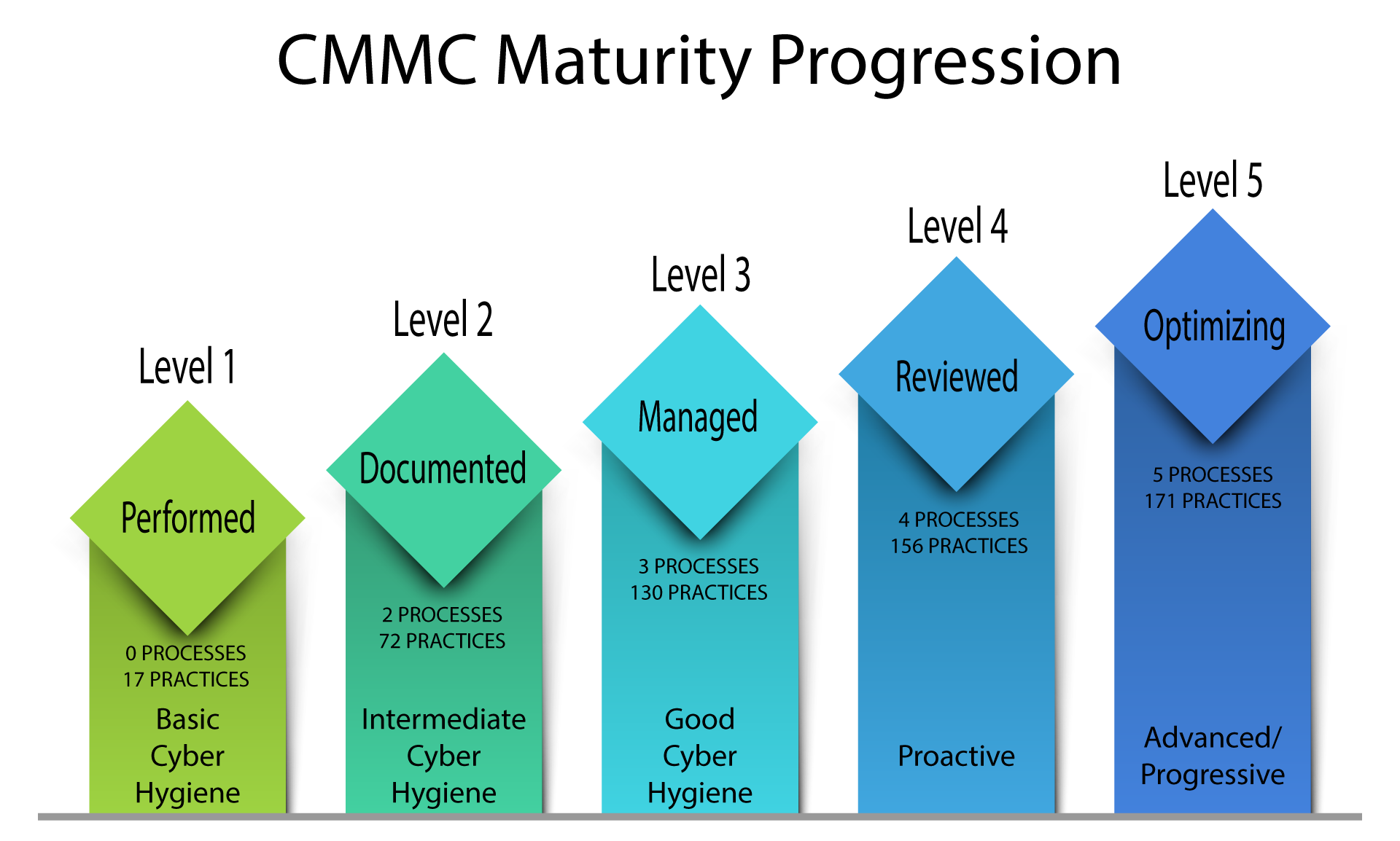
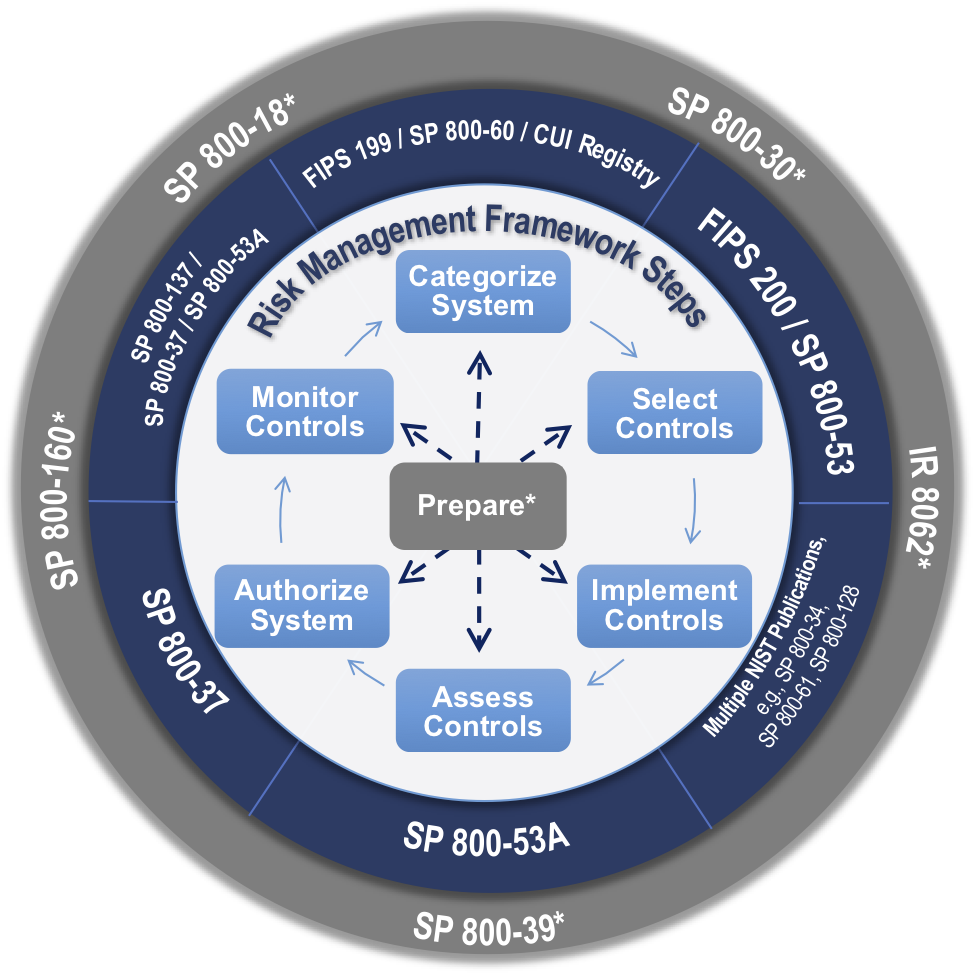
Nist is responsible for developing standards and guidelines including minimum requirements. Modules validated as conforming to specific standards are accepted by federal agencies for the protection of sensitive information. As part of this effort nist produces standards and guidelines to help federal agencies meet the requirements of the federal information security management act fisma. Nist in furtherance of its statutory responsibilities under the federal information security management act fisma of 2002 public law 107 347.
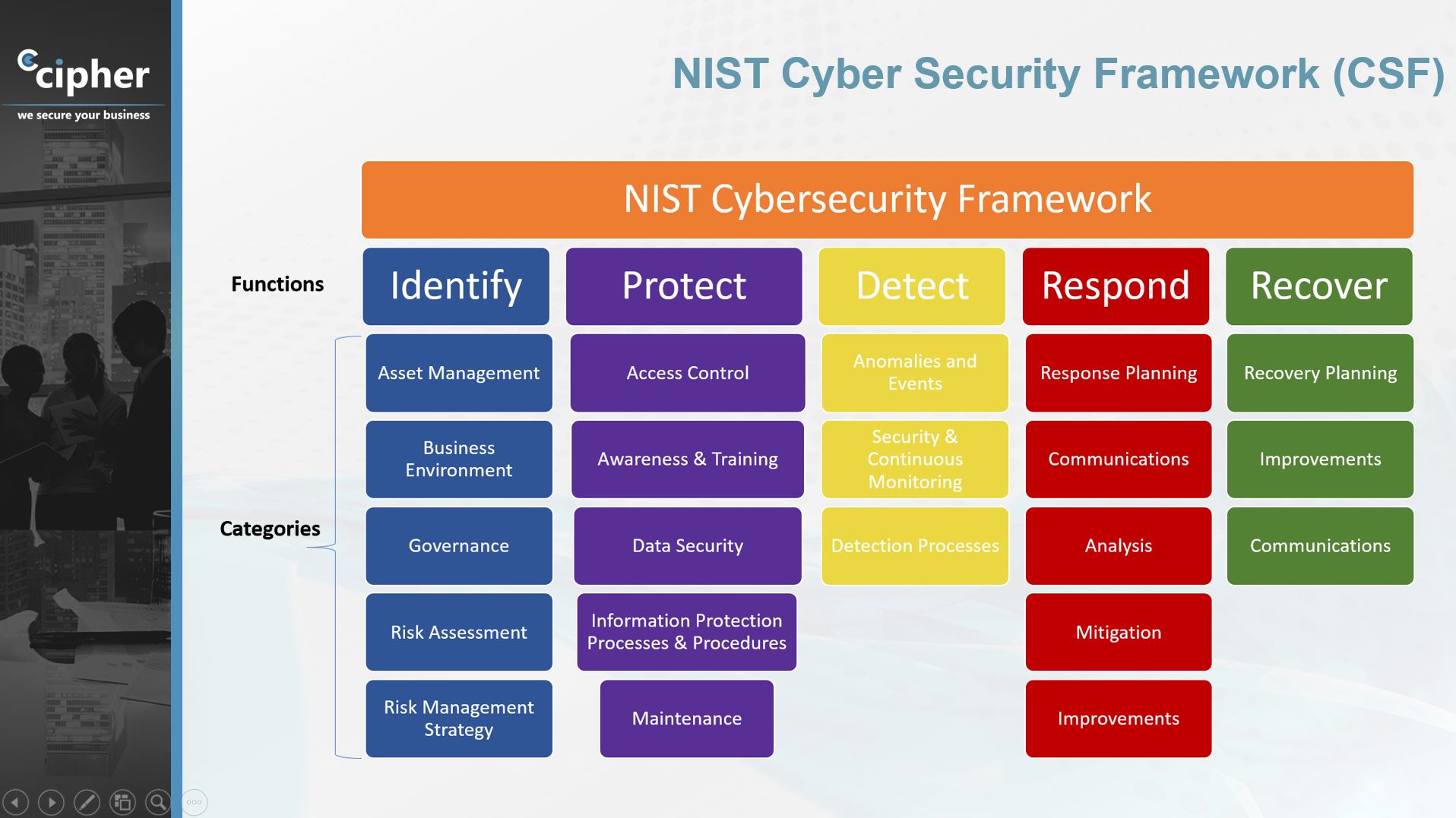
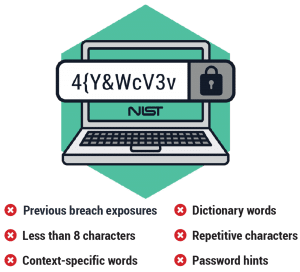
Nist is responsible for developing information security standards and guidelines incl uding 68 minimum requirements for federal information systems but such standards and guidelines shall not apply 69 to national security systems without the express approval of appropriate federal officials exercising policy 70 authority over such systems. Nist is responsible for developing information security standards and guidelines incl uding minimum requirements for federal information systems but such standards and guidelines shall not apply to national security systems without the express approval of appropriate federal officials exercising policy authority over such systems. If you re writing code you ought to be thinking about security as part of that nist s chief cybersecurity officer donna dodson said. These practices collectively called a secure software development framework ssdf 115 should be particularly helpful for the target audiences to achieve security software development 116.






/arc-anglerfish-arc2-prod-mco.s3.amazonaws.com/public/DAQC5KUYMVHRDKJ36T6HNTSUNU.png)